Leading IT Support Companies in Essex: Maximize Your IT Framework
Wiki Article

Safeguard Your Digital Possessions: The Power of Comprehensive Cyber Safety Methods in IT Support Providers
In the world of IT sustain solutions, the landscape of cyber threats impends ever-present, demanding a comprehensive strategy to guarding electronic assets. As companies progressively depend on innovation to conduct business and shop delicate info, the requirement for robust cyber safety and security strategies has actually ended up being vital. The evolving nature of cyber threats requires a positive stance to minimize dangers effectively and shield valuable data from coming under the incorrect hands. When thinking about the elaborate internet of interconnected systems and the possible susceptabilities they present, it comes to be clear that an alternative approach to cyber safety is not merely an alternative but a critical vital. The power of comprehensive cyber safety strategies exists in their ability to strengthen defenses, impart trust fund among consumers, and ultimately lead the means for sustainable growth and success in the digital age.Importance of Cyber Safety And Security in IT Support
The critical function of cyber safety in making certain the integrity and stability of IT support services can not be overstated. In today's electronic landscape, where cyber hazards are regularly advancing and becoming more advanced, durable cyber protection measures are crucial for guarding delicate information, protecting against unauthorized accessibility, and maintaining the general performance of IT systems. Cyber safety and security in IT support services includes applying a multi-layered protection approach that consists of firewall softwares, anti-viruses software application, intrusion detection systems, and regular security audits.Risks Reduction Via Robust Procedures
To properly secure against cyber risks and ensure the continual honesty of IT sustain services, companies should carry out robust measures for mitigating threats. One critical element of risk reduction is the establishment of an extensive incident feedback strategy. This plan lays out the actions to be taken in the occasion of a cyber breach, ensuring a swift and worked with action to reduce possible problems. Routine safety and security assessments and audits are additionally important in recognizing vulnerabilities and weak points within the IT facilities. By performing these analyses consistently, organizations can proactively resolve any type of concerns before they are manipulated by harmful actors.Furthermore, worker training and recognition programs play a significant function in threat mitigation. Enlightening team on best methods for cybersecurity, such as identifying phishing efforts and producing strong passwords, can assist avoid human error from becoming a portal for cyber dangers. Executing solid gain access to controls, file encryption protocols, and multi-factor authentication systems are added measures that can bolster the total security stance of an organization. By including these durable threat reduction measures, organizations can better protect their electronic assets and maintain the resilience of their IT sustain solutions.
Securing Delicate Details Successfully
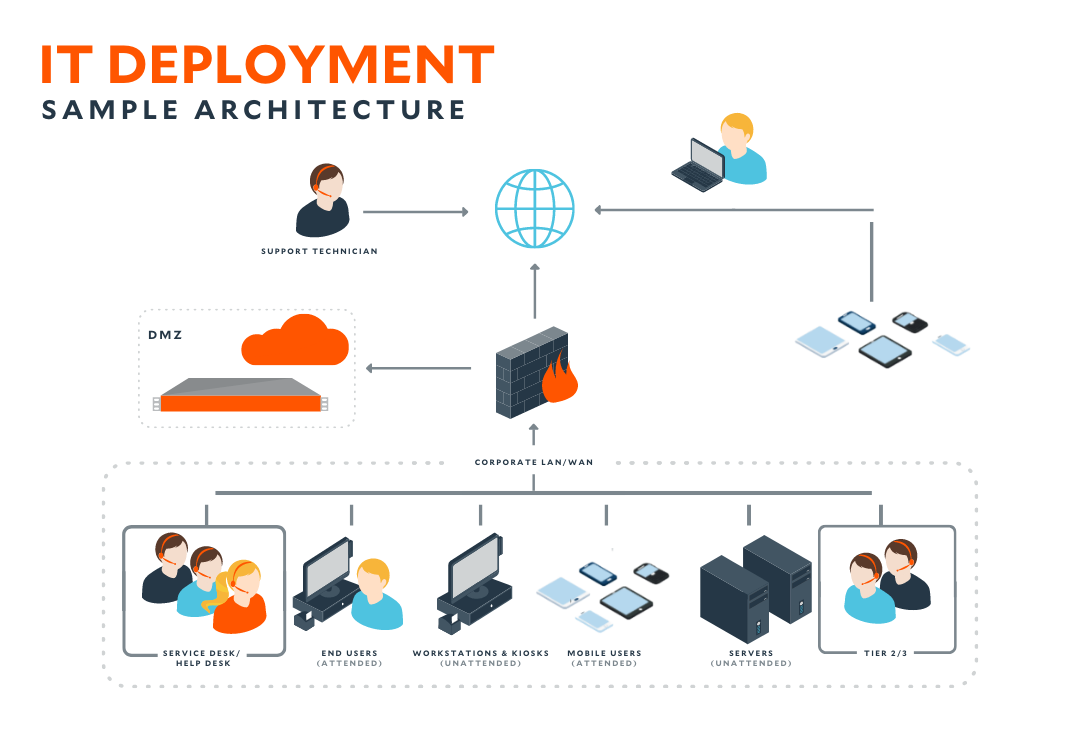
Additionally, educating workers concerning cybersecurity best methods is crucial in safeguarding sensitive info. Educating programs can aid staff members identify phishing efforts, avoid clicking on harmful web links, and comprehend the relevance of solid password health. Routine security understanding training sessions can substantially decrease the danger of human mistake bring about information violations. By combining technological services, gain access to controls, and staff member education and learning, organizations can effectively protect their sensitive information in the digital age. it support companies in essex.

Building Client Trust Fund With Safety And Security Techniques
Organizations my link can solidify customer count on by applying durable safety methods that not just secure delicate helpful resources details successfully yet likewise demonstrate a commitment to data protection. By focusing on cybersecurity actions, organizations share to their consumers that the security and privacy of their data are paramount. Structure consumer depend on with safety techniques includes transparent interaction pertaining to the steps taken to secure sensitive information, such as security procedures, routine security audits, and staff member training on cybersecurity best practices.In addition, companies can improve customer trust fund by immediately dealing with any kind of safety and security events or breaches, revealing accountability and an aggressive technique to fixing problems. Showing compliance with industry guidelines and standards likewise plays a critical duty in assuring consumers that their data is taken care of with the utmost treatment and in conformity with well-known safety protocols.
Furthermore, giving clients with clear regards to service and privacy policies that information how their information is collected, kept, and made use of can even more infuse confidence in the safety measures implemented by the organization. cyber security consultant Essex. Ultimately, by integrating durable security techniques and cultivating transparency in their information protection methods, companies can reinforce consumer trust and loyalty
Benefits of Comprehensive Cyber Safety And Security
Implementing an extensive cyber safety approach brings regarding a myriad of advantages in protecting critical data assets and maintaining functional strength. One substantial advantage is the protection of delicate information from unauthorized access, guaranteeing data privacy and integrity. By executing robust safety and security steps such as encryption, access controls, and normal protection audits, companies can alleviate the danger of data breaches and cyber-attacks. Additionally, a comprehensive cyber protection method assists in maintaining regulatory compliance, staying clear of possible legal issues, and maintaining the company's track record.A strong cyber safety pose can provide companies an affordable side in the market by showing a dedication to shielding consumer information and keeping trust. Overall, investing in comprehensive cyber security measures is important for guaranteeing the long-lasting success and sustainability of any type of contemporary service.
Final Thought
To conclude, extensive cyber safety and security techniques in IT support solutions are crucial for guarding electronic possessions and find mitigating dangers successfully. By executing robust measures to protect delicate info, companies can build trust fund with clients and profit of a safe environment. It is crucial to focus on cyber safety and security to ensure the honesty and privacy of data, inevitably causing a more safe and secure and reputable IT framework.In today's digital landscape, where cyber hazards are regularly evolving and coming to be much more innovative, robust cyber safety and security measures are vital for guarding sensitive information, protecting against unapproved access, and preserving the overall functionality of IT systems. Cyber protection in IT support services entails applying a multi-layered defense technique that consists of firewall programs, antivirus software, invasion detection systems, and normal safety and security audits.
Structure consumer count on with safety approaches involves transparent interaction pertaining to the steps taken to shield delicate information, such as file encryption procedures, normal security audits, and employee training on cybersecurity finest methods.
Applying an extensive cyber safety approach brings about a myriad of advantages in protecting important information properties and keeping functional strength. By applying robust safety and security steps such as file encryption, gain access to controls, and routine safety audits, organizations can alleviate the danger of data violations and cyber-attacks.
Report this wiki page